Building a secure system is not just about adding encryption or firewalls at the end of development. Security must be baked in from the start.
This is where threat modelling and specifically the STRIDE framework plays a crucial role, we covered this in part 1, but to see how this works in practice, let’s walk through an exemplar scenario.
NightBank Digital
NightBank Digital is a fast-growing online banking and payment platform that offer a range of services. These include:
- Mobile and web apps for customers to manage accounts and transfer money.
- A third-party API for fintech partners to integrate NightBank’s payment services.
- An internal admin portal for staff to detect fraud, review transactions, and handle disputes.
As NightBank plans to expand globally, key stakeholders recognise the need to embed security in the design process, not patch it later. The first step in threat modelling is understanding what you’re protecting.
The Security team maps out the following:
- Actors – Customers, Admin staff, Third-Party Partners.
- Components – Mobile app/web app, API gateways, Core Banking Backend, Customer database, Payment Processor.
- Trust Boundaries – Internet to API Gateway, Internal Network to Payment Processor.
This decomposition creates a visualisation on how data moves and where attackers might target and strike.
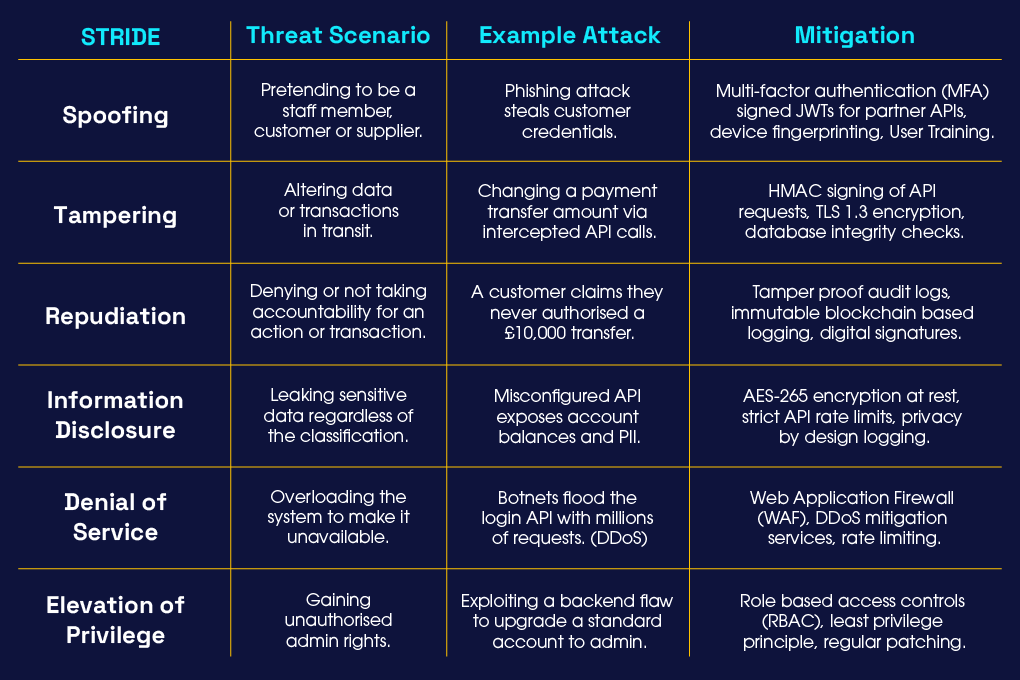
The next step for the team is to review each component against the six STRIDE threat categories that we covered in the previous blog.
Not all threats are equal, NightBank uses a risk matrix to rank threats by likelihood and impact, helping stakeholders allocate resources accordingly:
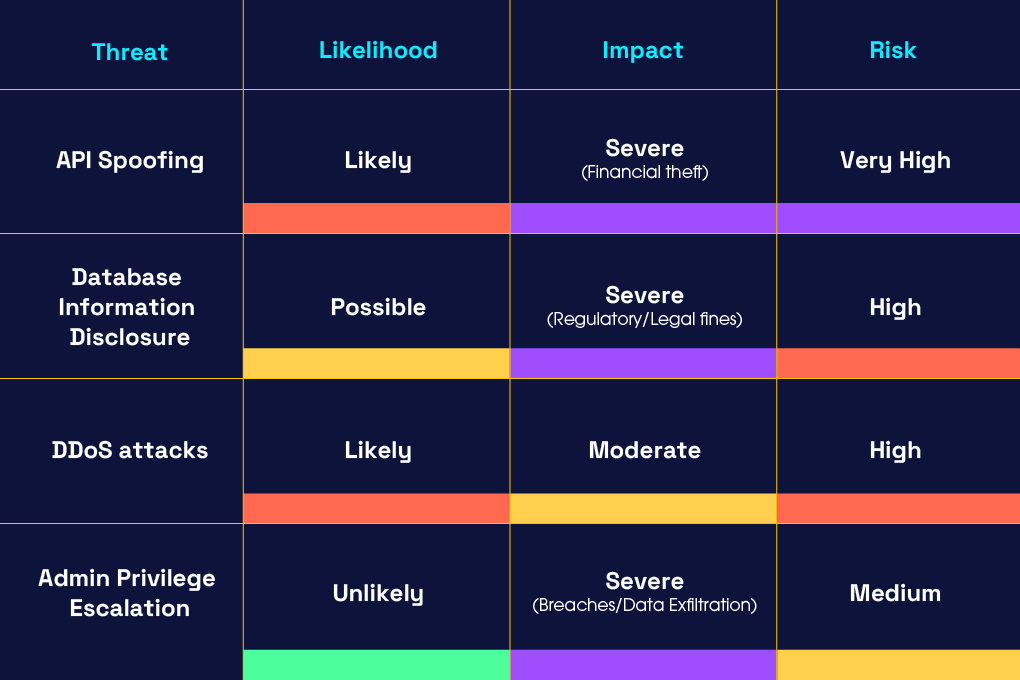
This guides design decisions, such as prioritising MFA rollout and advanced DDoS protections before launch.
Why STRIDE is crucial in the secure design process
Security By Design (Not afterthought)
It identifies threats early on, before code is written, reducing costly rework or emergency patches after deployment.
Structured Thinking
It prevents blind spots by forcing teams to consider all six threat categories systematically. Not only that but also helps uncover vulnerabilities that might have not been flagged through methods such as penetration testing.
Clear requirements for engineers
It converts abstract threats into concrete design requirements such as requiring signed API calls or immutable audit logs.
Business risk alignment
It helps stakeholders understand which attacks have the highest financial and reputational impact, making security an informed business decision. On the other hand, it also reduces costs relating to breaches, as there’s a proactive attitude towards incorporating secure design from the start.
Continuous improvement
Threat models evolve with the product. As NightBank adds new features such as cryptocurrency transfers, STRIDE sessions reveal new ways in which attacks surface, which encourages departments involved with delivery to work towards a better shared understanding across internal teams.
To Conclude
STRIDE combined with design creates secure foundations, means building security into the system’s core; It’s infrastructure, architecture, data flows, and access controls, rather than adding it later. Applying STRIDE early ensures threats like spoofing, tampering, or data leaks are addressed before coding begins, turning protections such as encryption, authentication, and logging into essential design requirements. This makes the system harder to attack, cheaper to maintain, and more resilient from the ground up.
By applying STRIDE threat modelling early in the secure design process, NightBank Digital transforms security from a reactive cost into a proactive strategy. This approach helps empower engineering teams to build with confidence and keeps attackers one step behind. Cyber Security Specialists are committed to helping you improve your security posture, contact us today for any questions you might have!