COMPARISON TABLE: WHO EACH SERVICE IS FOR?
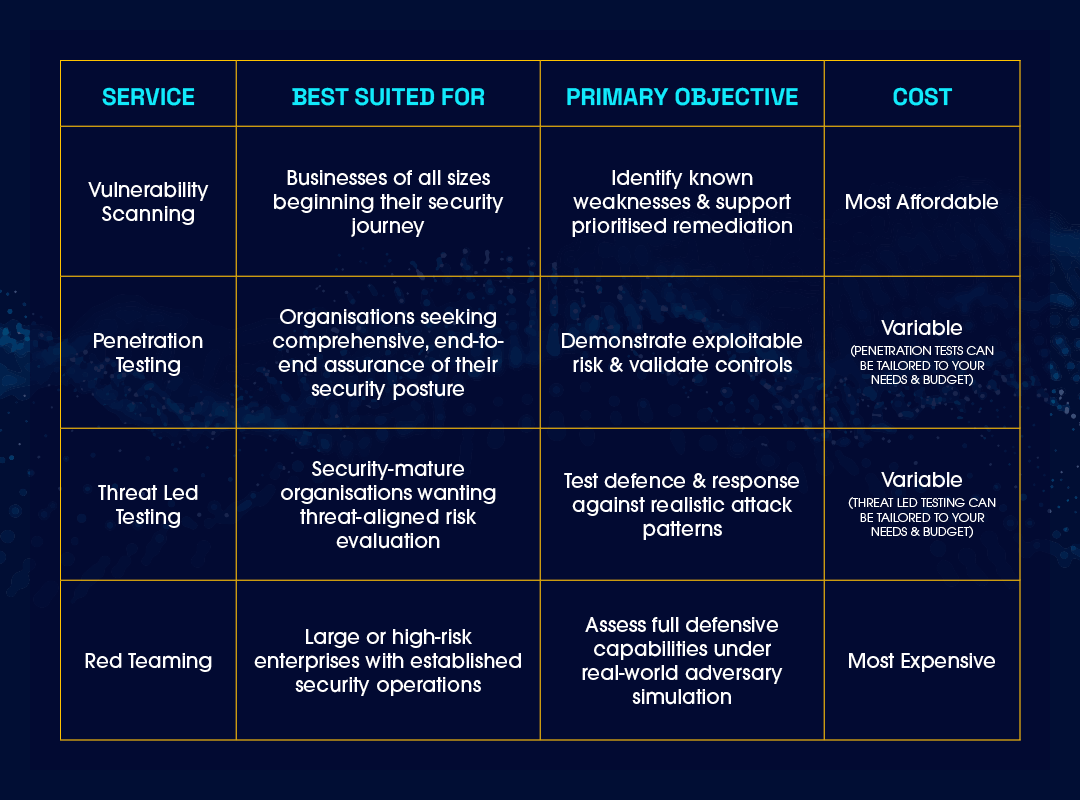
VULNERABILITY SCANNING
Vulnerability Scanning is an automated security assessment designed to identify known weaknesses across an organisation’s IT environment. This includes servers, networks, endpoints, web applications, cloud services and other connected assets. Using industry-standard scanning tools, the process compares assets against a database of known vulnerabilities, misconfigurations, missing patches and insecure settings. The result is a comprehensive inventory of exposures ranked by severity.
Vulnerability scanning is not exploitative by design; it highlights areas that could be attacked, rather than proving that they can be exploited. Output includes remediation guidance to support prioritised patching and risk reduction. Regular scanning enables organisations to track improvements, detect regressions and meet compliance requirements such as ISO 27001, PCI-DSS or regulatory obligations.
This service is best for maintaining ongoing visibility of an attack surface and driving a structured vulnerability management programme.
PENETRATION TESTING
Penetration Testing is a controlled, authorised security evaluation in which experienced testers actively simulate real-world attacks against defined systems, applications or network segments. Unlike automated scanning, penetration testing involves active testing methodologies and exploit attempts to confirm whether identified weaknesses can be abused to compromise confidentiality, integrity or availability. The goal is to assess the true risk by demonstrating achievable impact. All exploitation is agreed on before testing begins in order to eliminate or minimise potential downtime.
A typical penetration test includes information gathering, vulnerability identification, exploitation, privilege escalation and reporting.
Testers leverage both automated tools and manual techniques to uncover business logic flaws, authentication weaknesses, insecure APIs, poorly configured infrastructure and other deep issues that scanners often miss. The output is a detailed report with evidence of findings, proof of exploit paths and tailored remediation recommendations.
Penetration testing is widely used for meeting regulatory requirements, validating security controls before production deployment, and providing assurance to stakeholders that critical systems are robust against targeted attack techniques.
THREAT LED TESTING
Threat Led Testing is a threat-contextual security exercise that simulates attacks based on realistic adversary behaviour and specific business risk scenarios. Rather than simply scanning or exploiting isolated vulnerabilities, this approach constructs detailed attack narratives that mirror how actual attackers operate against an organisation’s environment. Scenarios may be drawn from threat intelligence, industry-specific risk profiles, known APT campaigns or common attacker playbooks.
In practice, scenario-based testing assesses not only whether controls can be bypassed, but also how well people, processes and technologies prevent, detect and respond to those threats. The tests often focus on targeted campaigns such as phishing leading to lateral movement, or API abuse executed against critical business functions. Findings include gaps in detection, monitoring blind spots, and weaknesses in incident handling as well as technical vulnerabilities.
This service sits between traditional penetration testing and full Red Team operations. It is particularly valuable for organisations that already have baseline security controls and want to stress-test them against specific, credible threats that reflect their sector, data sensitivity and attacker profile.
RED TEAMING
Red Teaming is the most comprehensive offensive security assessment, emulating persistent, resourceful attackers with the objective of achieving high-level business outcomes rather than simply finding vulnerabilities.
Red Team operations are objective-based and unconstrained by strict scopes; testers must think like real adversaries and use a wide range of tactics, techniques and procedures (TTPs) across cyber, social and physical vectors.
Unlike penetration tests or automated scans, Red Teaming evaluates the full security stack: technical vulnerabilities, security monitoring efficacy, incident response maturity, human behaviours, security policy execution and cross-domain resilience. Engagements typically begin without disclosure to defenders, allowing detection controls and response teams to be tested under authentic conditions. Success is measured by scenarios such as exfiltrating sensitive data, disrupting critical services, or moving laterally through an environment while evading detection.
Red Teaming is best suited to large enterprises, highly regulated sectors, or organisations that prioritise proactive security improvement. It provides strategic insights into where defensive capabilities are weakest and how well security operations can withstand a sophisticated, prolonged attack.

The Cyber Security Specialists Penetration Testing Service is CREST-accredited. Holding this title is a great privilege and demonstrates that Cyber Security Specialists:
- is an entrusted partner for delivering high-quality Penetration Testing services
- has reliable methodologies and processes
- provides comprehensive reporting
- has highly skilled Cyber Security professionals
Get in touch
Find out more
For more information regarding any of our Testing services please contact us on 0161 706 0244 or email info@cybersecurityspecialists.co.uk to speak with a member of the team.