Threat modelling is a critical part of building secure systems. It shifts security left in the development process, reduces risk, and helps ensure that systems are resilient to real-world threats.
Benefits of Threat Modelling
The benefits of threat modelling are summarised below:
-
Proactive Risk Management
- Instead of reacting to security breaches, threat modelling allows teams to anticipate threats early in the design or development phase.
- It saves time and resources by addressing issues before they become real problems.
-
Improved Security Posture
- Helps uncover vulnerabilities that might not be obvious through other testing methods such as penetration testing or code reviews.
- Ensures that security is baked into the system architecture from the start.
-
Better Understanding of the System
- Encourages teams to fully map out how a system works, including data flows, trust boundaries, and assets.
- Leads to better documentation and shared understanding across teams (development, architecture, security, operations).
-
Regulatory and Compliance Alignment
- Many security standards and frameworks (like ISO 27001, NIST, PCI-DSS) recommend or require some form of threat modelling.
- Helps demonstrate due diligence and security by design to auditors and stakeholders.
-
Cost-Effective
- Fixing security flaws early in the design phase is significantly cheaper than fixing them post-deployment or after a breach.
- Reduces potential costs related to data breaches, including fines, legal fees, and reputational damage.
-
Supports Secure Development Practices
- Fits into Secure Software Development Life Cycle (SSDLC) processes like DevSecOps.
- Encourages all project stakeholders such as developers and architects to think like attackers, building more resilient systems (not just Security folk!).
Methodologies
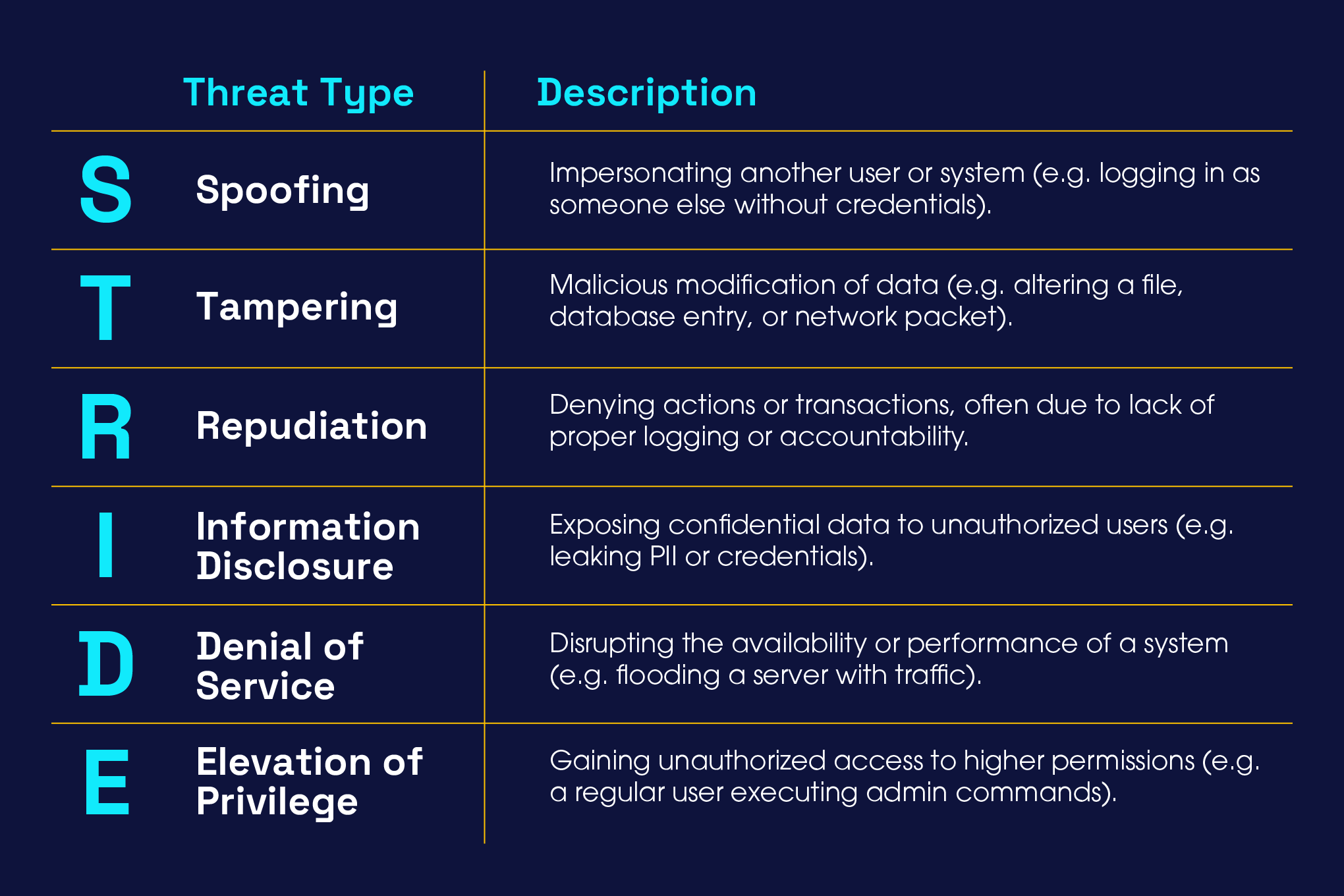
STRIDE is a popular threat modelling framework originally developed by Microsoft to help identify security threats in software systems. It’s an acronym that categorises six common types of threats:
In Summary
STRIDE doesn’t tell you how to fix threats, but it ensures you think about all the ways a system can be attacked. It’s a powerful foundation for secure design, and something that is recommended by NCSC and the UK Government Security Function.
We’ll talk more about the practical implementation of STRIDE in our next Blog! Contact our friendly team with any Cyber Security questions you might have.